
Layer 8 Hacking can be defined as hacking above and beyond the technical layers; hacking by targeting the user, the business processes, or the organization i

Practical Cybersecurity Architecture - Second Edition

Computer Systems Security: Planning for Success

Internet of Things Security and Privacy

Blog – Cyber Physical Risk Academy

OSI Model: The 7 Layers of Network Architecture – BMC Software
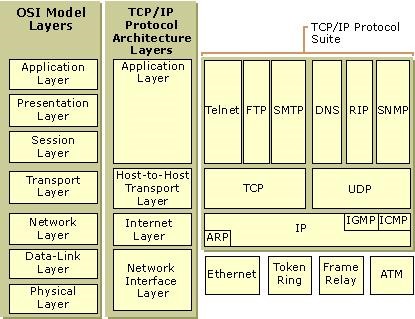
Hacker Fundamentals: A Tale of Two Standards « Null Byte

Cyber Hygiene and the Cyber Ecosystem Attack Analysis Methodology

The elements of IACS security programme development according to

The OSI Model & TCP/IP Model – The Cybersecurity Man

8th Layer in OSI Model…. Twitter recently disclosed that its own
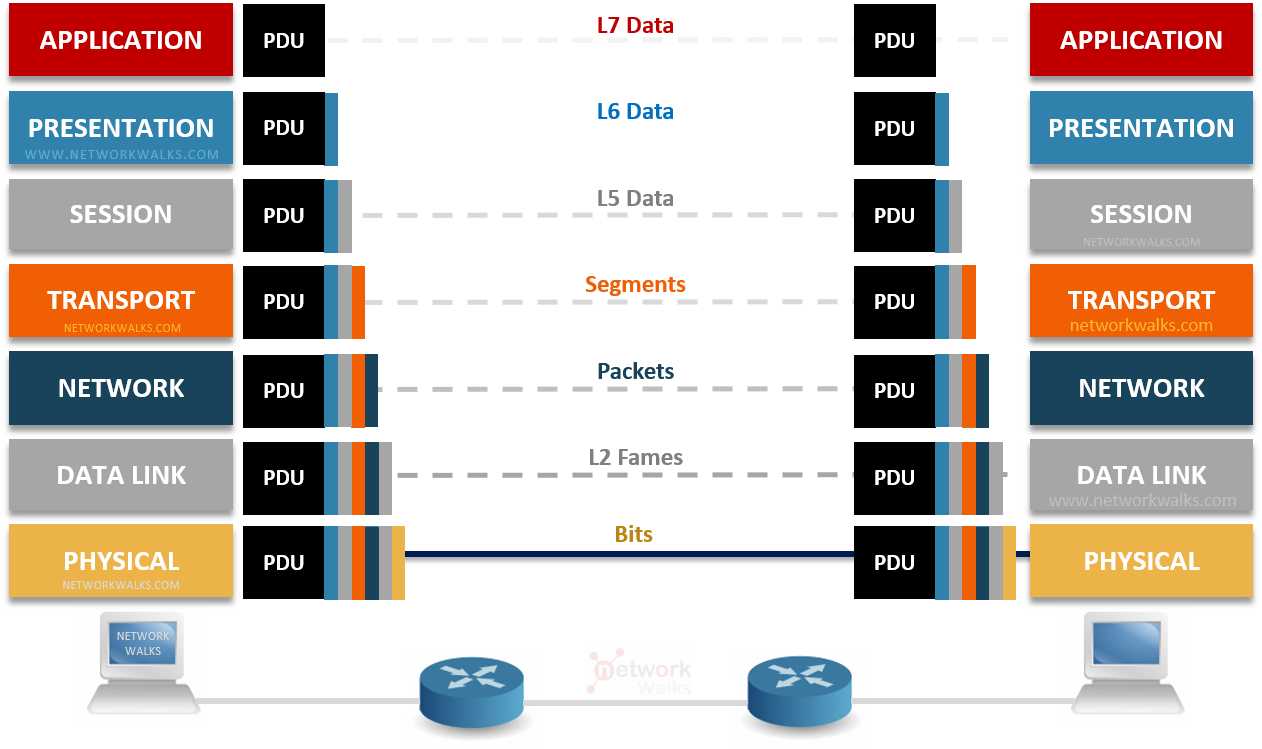
OSI Model (Open Systems Interconnection Model)

A survey of cyber security threats and solutions for UAV
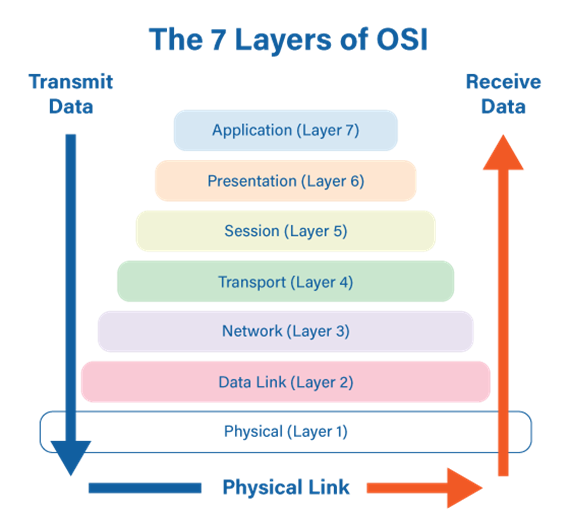
An overview of the OSI model and its security threats
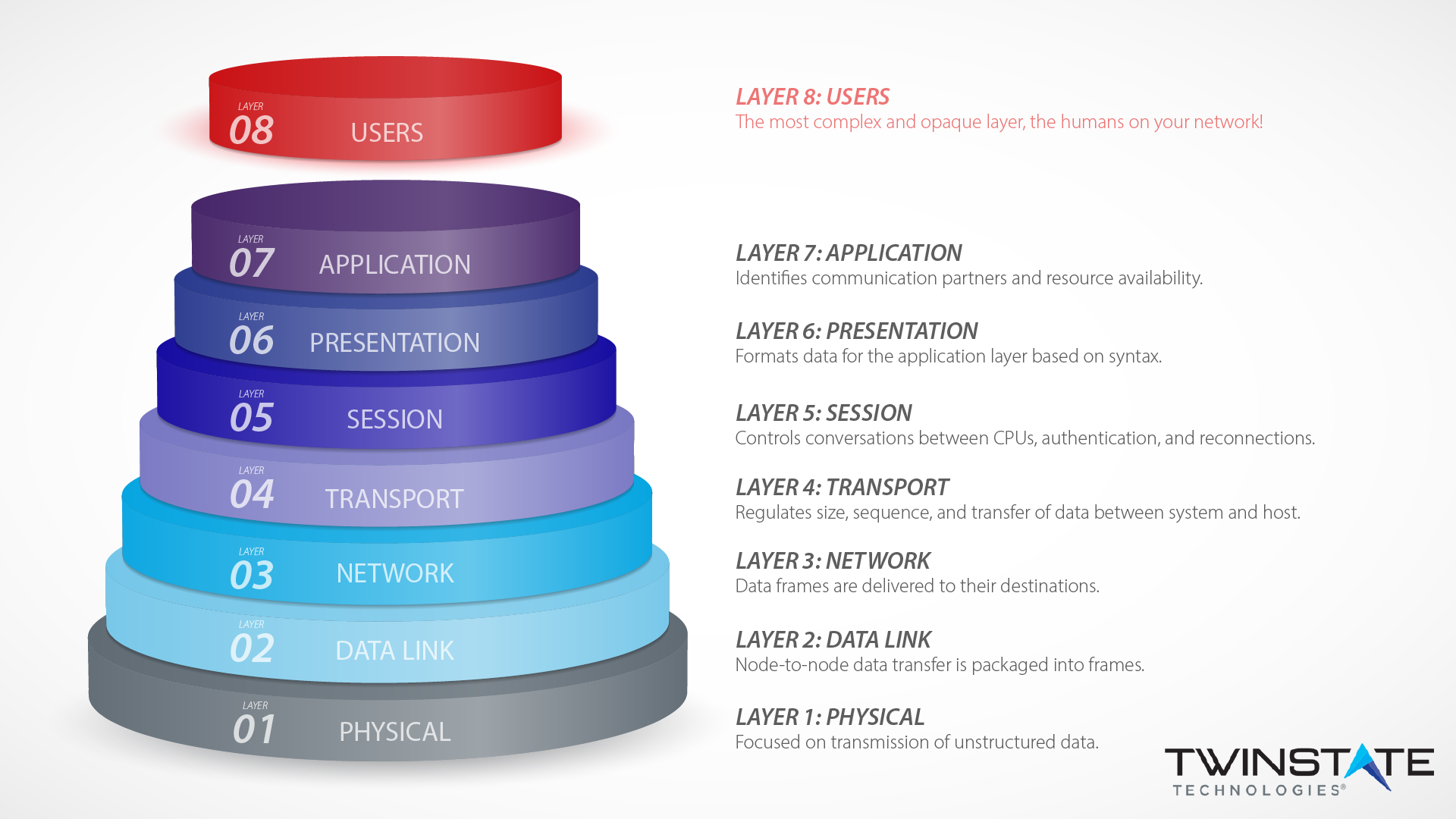
Layer 8 Technology: How We Protect Users at our Plattsburgh Office